
Solved 7) The Speedy Oil Change Company advertises that the
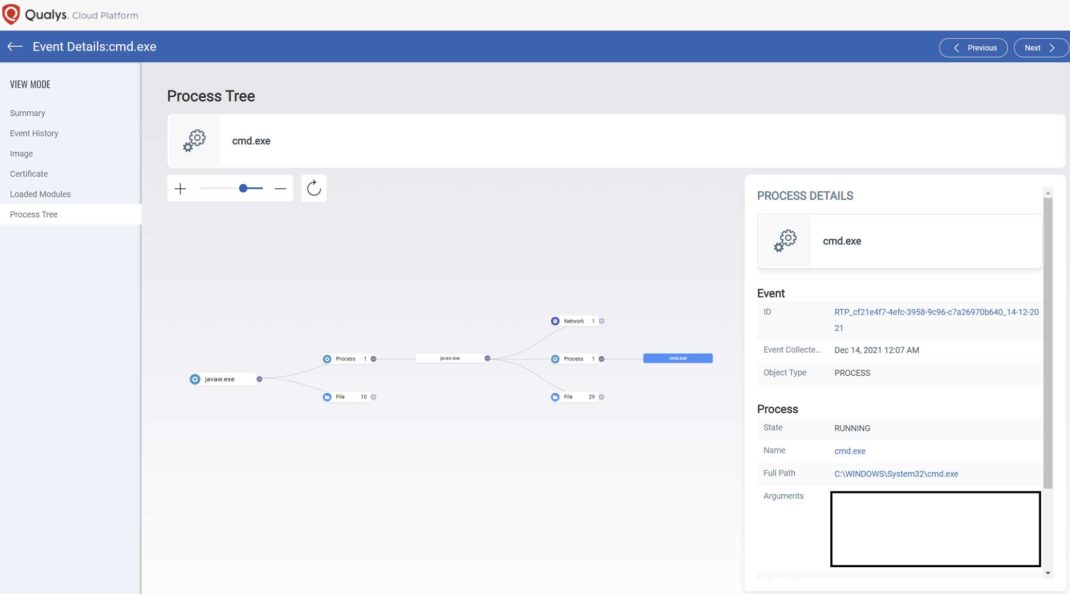
Log4Shell Exploit Detection and Response with Qualys Multi-V
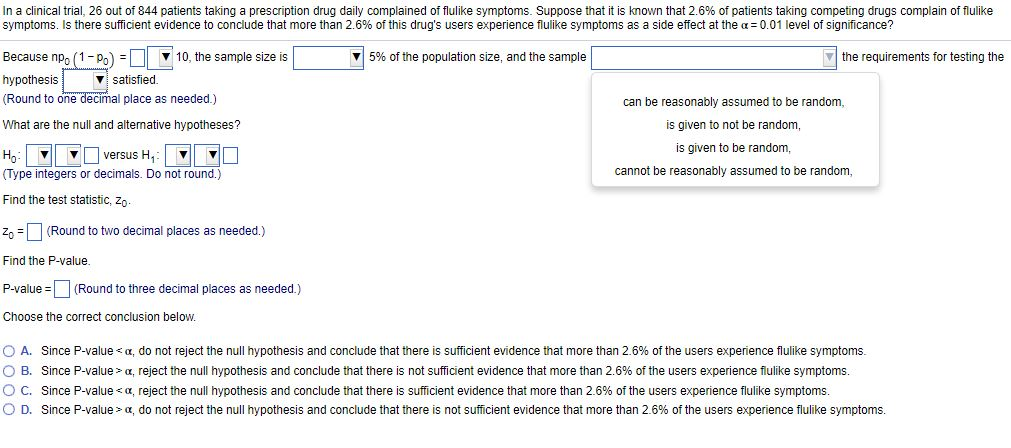
Solved In a clinical trial 26 out of 844 patients taking a

Spam and phishing in Q2 2020 - vulnerability database
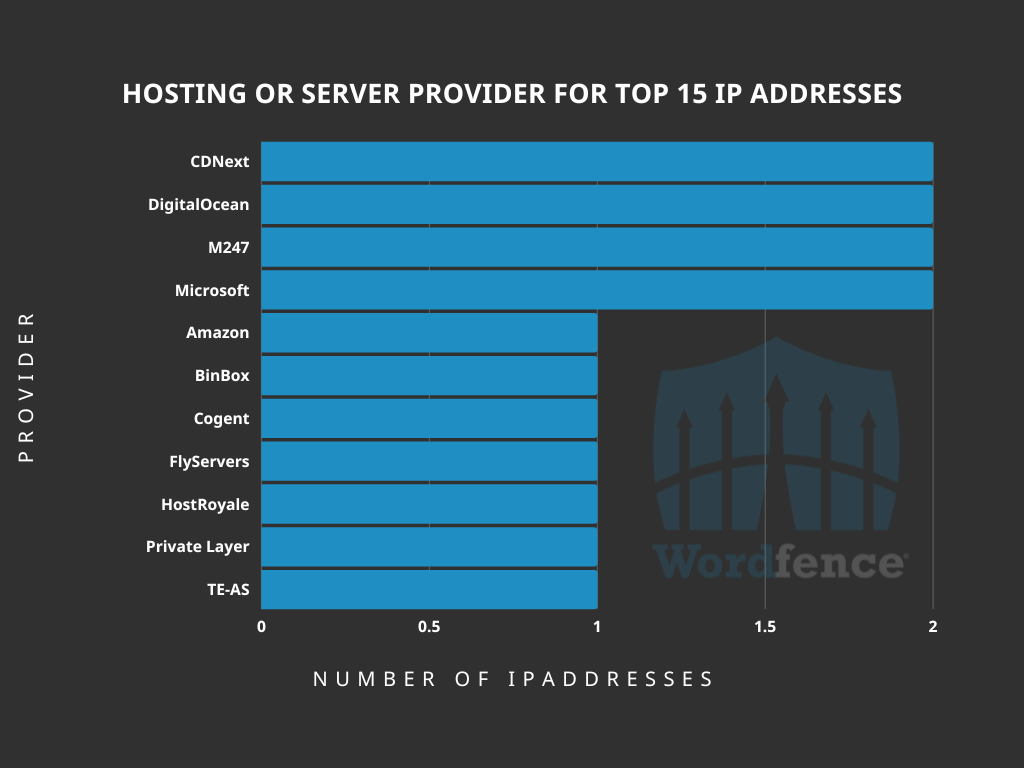
Analyzing Attack Data and Trends Targeting Log4J - vulnerability

Critical Citrix RCE Flaw Still Threatens 1,000s of Corporate LANs
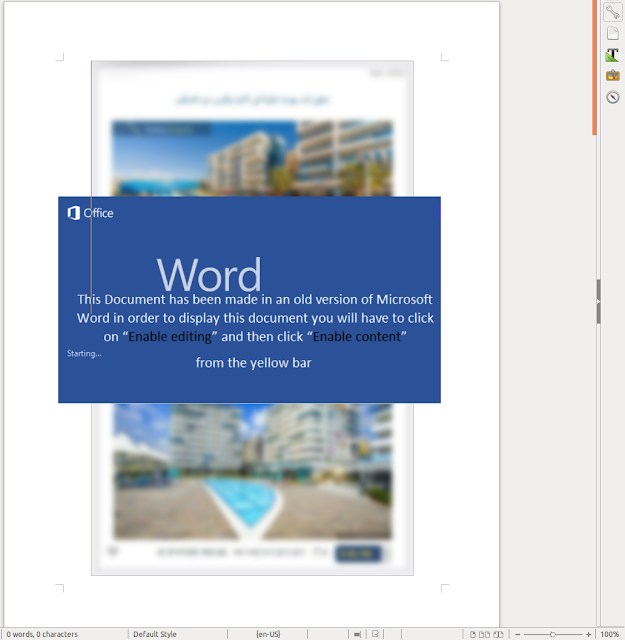
It's alive: Threat actors cobble together open-source pieces
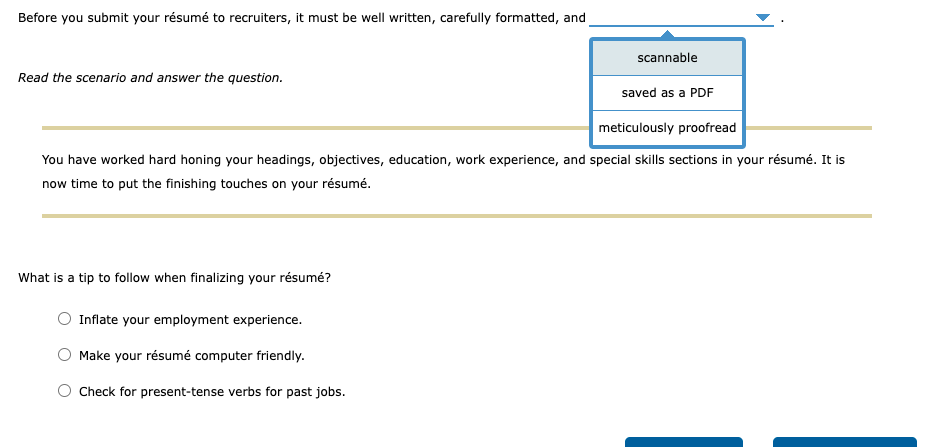
Solved 3. Applying the Final Touches to Your Résumé With so

conclusion By including this information does Specter strengthen

Improve Your Resume: Avoid These 3 Major Errors and Make a
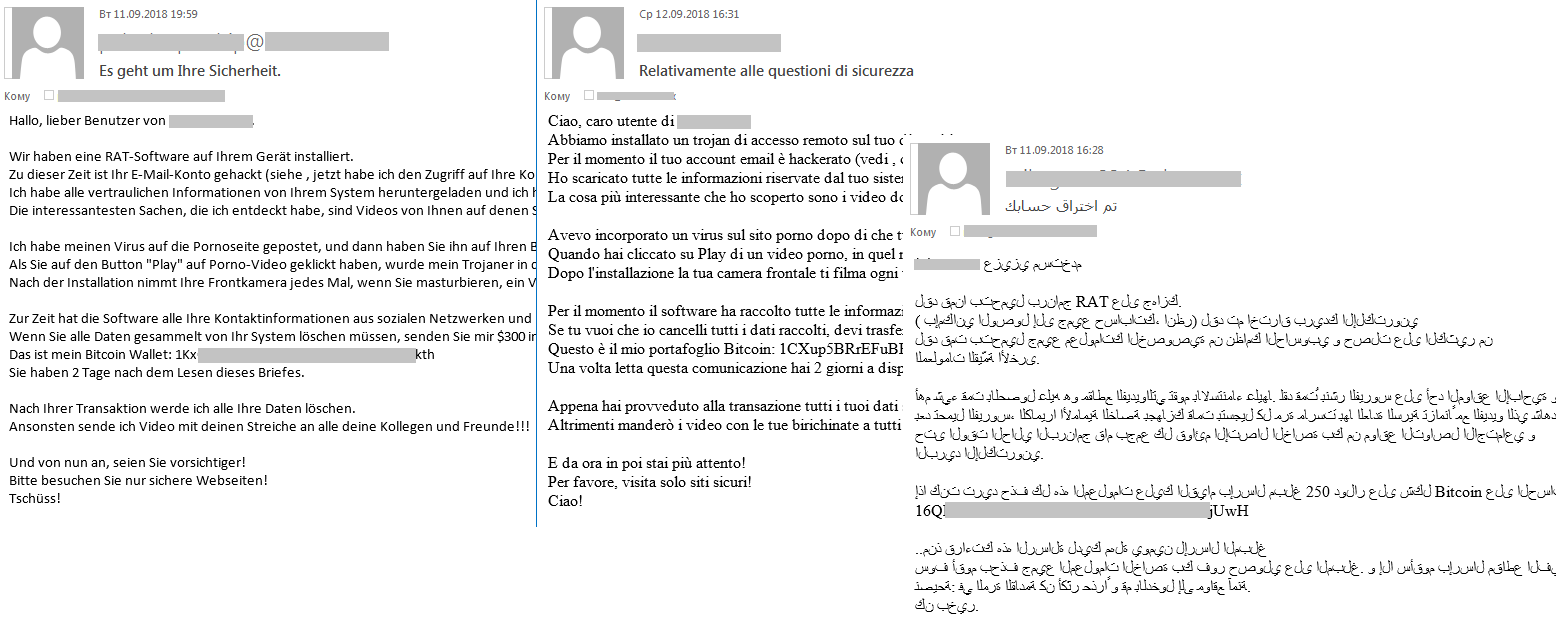
Spam and phishing in Q3 2018 - vulnerability database
