
RIG Exploit Kit Delivering Monero Miner Via PROPagate Inject

Cycldek: Bridging the (air) gap - vulnerability database

RevengeHotels: cybercrime targeting hotel front desks worldw

State-Sponsored Hackers Likely Exploited MS Exchange 0-Days

CC Fine Arts: Week 4: Abstract Art
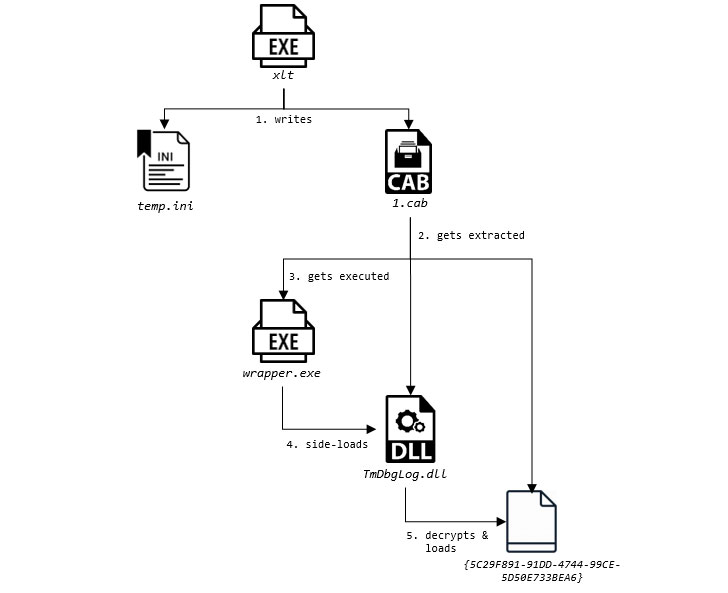
New USBCulprit Espionage Tool Steals Data From Air-Gapped Co

IEA-IGF Webinar The Role of Critical Minerals in Clean Energy

opioid system and touch - Google Search

How To Prioritize Vulnerabilities in a Modern IT Environment
twitminer/Training_Validation_datasets/shuffle_training.txt at
data-science-course/examples/WebScraping/must-reads_20140512.txt

Recent Cloud Atlas activity - vulnerability database

SGI :: The danger of too much narration and not enough dice rolling
