
Hackable $20 Modem Combines LTE And Pi Zero W2 Power
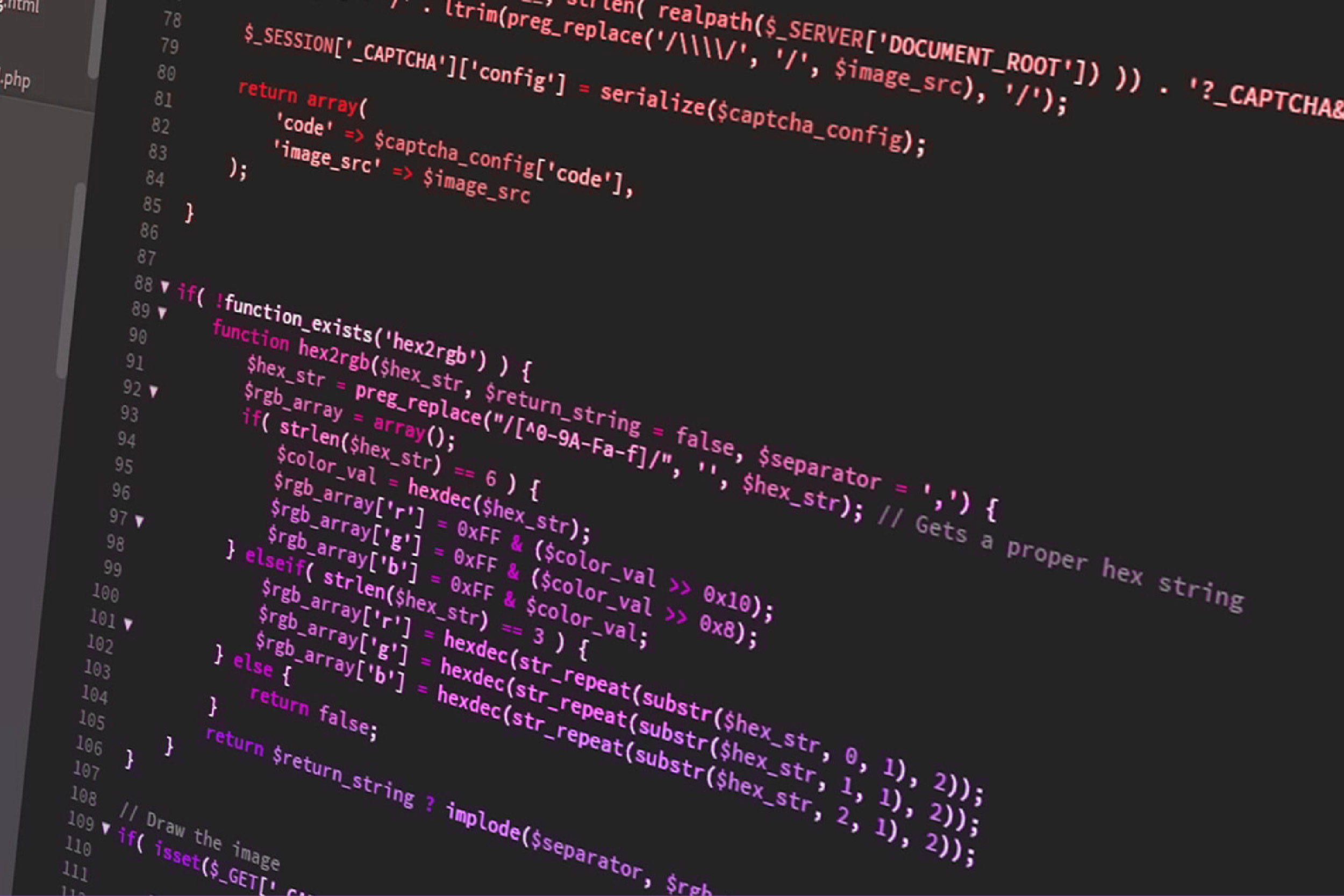
Attackers Targeted Oracle WebLogic Servers with New ScrubCrypt Crypter
Denial-of-service attack - Wikipedia
Major SMS routing company says it was the victim of a five-year hack (updated)

What Is a Red Team Exercise & Why Should You Conduct One?
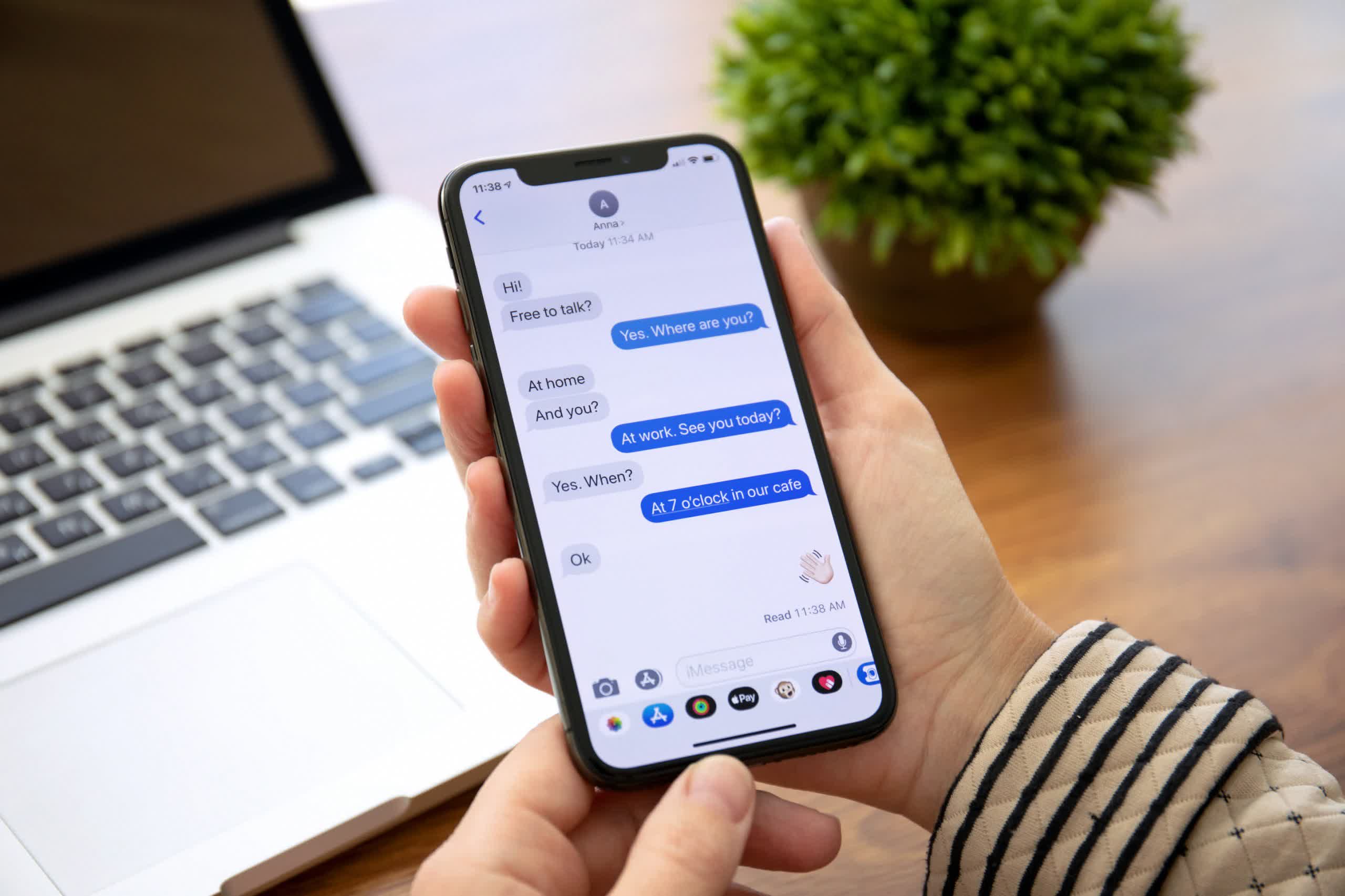
Major SMS routing company admits it had been hacked for five years

Chinese Hackers Just Gave Us All A Reason To Stop Sending SMS Messages
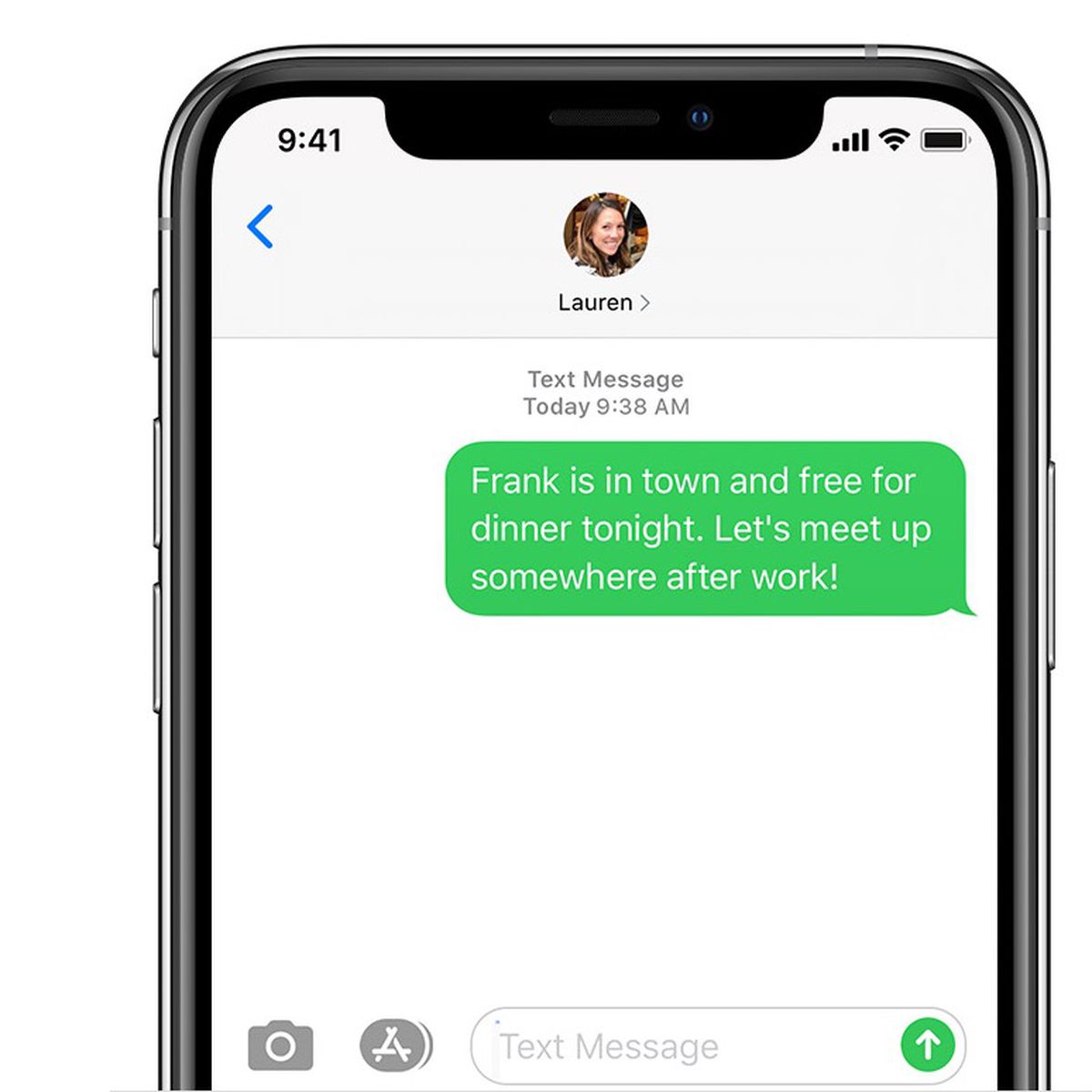
U.S. Carriers Fix SMS Routing Vulnerability That Let Hackers Hijack Texts - MacRumors
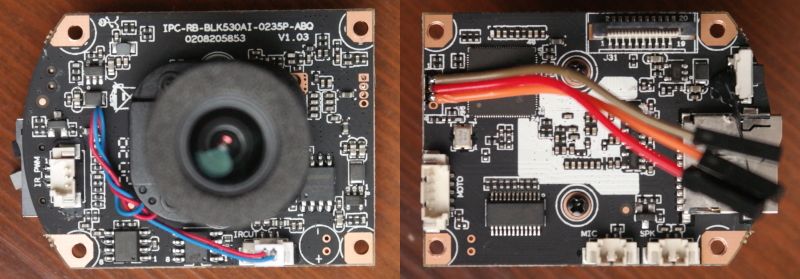
Getting Root On A Chinese IP Camera

Chinese hackers launch Linux variant of PingPull malware - Channel Asia

Chinese Hackers Create Fake News Site To Infect Gov't Targets

How Chinese hackers exploited Linux servers undetected for eight years

Securing Wifi in Organization Wifi network security & Wifi Security Types

The Full Story of the Stunning RSA Hack Can Finally Be Told

CISA: Chinese Hackers Exploiting Unpatched Devices to Target - vulnerability database
